Analyse the Target Site¶
The first step in writing a resolver plugin (after choosing the site of course!) is to analyse the target site to see how it works. Remember, your plugin will be passed a URL to a web page on your target site and your code must be able to turn that into the direct URL to the media file or stream.
First Look¶
Our target site is http://videobb.com so let’s start by looking at a video on that site.
The front page contains links to some videos so that is probably a good place to start. Notice they are in the form http://videobb.com/video/{VIDEO_ID} so this is definitely going to be a pattern we want to advertise our plugin as capable of handling. The video id seems to comprise of numbers and both lower and upper case letters (or in regex terms [0-9A-Za-z]).
Clicking on one of these links (I chose http://videobb.com/video/8FvAG6AQpHi8) notice that you get diverted to http://videobb.com/watch_video.php?v={VIDEO_ID} (in my case http://videobb.com/watch_video.php?v=8FvAG6AQpHi8). Another pattern we’ll want to be able to handle.
Are We Human?¶
Notice there appears to be no ‘Are you human?’ verification that there is with many sites. This could be because we have clicked through from their front page which may have set a cookie or the referrer header to the right value.
Lets test that out. Start by opening an incognito window of Chrome. This is a handy trick to ensure that no cookies are left over from previous visits without having to keep clear them out.
Now paste the URL to the video page (http://videobb.com/watch_video.php?v=8FvAG6AQpHi8) into the URL bar and hit enter. Looks like it works so I guess they don’t do any checking at all - nice!
If you find your host does require that you prove you are human, often this is just a case of sending some cookies, or posting some form values.
Finding the Media URL¶
Now the fun part!
Open the developer tools of Chrome (Shift + Ctrl + I), open the ‘Network’ tab and reload the page. You should see a list of all the files that page loads.
Click on the play button of the flash video and you’ll see some extra activity in the network tab.
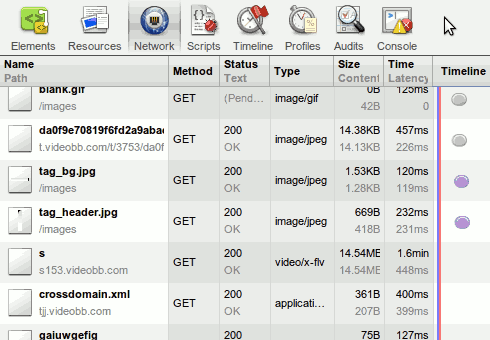
Spot the useful file....
Ah, one of those has a mime type of video/x-flv - that has to be our video! Clicking on that entry shows that the request URL is http://s153.videobb.com/s?v=8FvAG6AQpHi8&r=2&t=1313232595&u=&c=11885AACE290D85BA5F8CB5B6430028F9642DA1BF9CA4D6809490FCFE023E07C&start=0.
It looks like t is a Unix timestamp, and c looks like an access token, so this will probably be different for you. Indeed you can try reloading the page and pressing play again and you’ll see the URL is different.
What Do We Know?¶
At this stage, we now have enough info to write our plugin.
We know some URL patterns that we can resolve, we know what URL we need to retrieve in order to find the media URLs (http://videobb.com/player_control/settings.php?v={VIDEO_ID}), and we know how the media URLs are encoded (base64).
Time to move on and write some code!